Low Effort Passive Security & Privacy

Talking back part of your privacy & sanity with free & open source software.
Premise: Easy of use breeds complicity thus vurnebility.
In today’s day and age everything is a click away an app you can download and get on with life like nothing is happening. Well allot is going on but it’s not in plain sight, if it was you would want to run to the hills. On the contrary, the major networks that have taken over our life’s collectively would say that it’s business as usual and business is good. Not going to go in the specifics of these networks and companies because this is not the subject of this post.
It’s the complete opposite on how slowly but surely you break free from everything and everyone trying to shove shit down your throat and YOUR network. We’re gonna take a look on tools and practices of everyday computing. Security conciseness comes from switching out your current workflow with something that does not breed complicity via easiness.
By breaking down what you actually do online and what services are critical, you can make a blueprint on how to start pulling back and start building your core services free from 3rd party eyes. This is what we’re gonna talk about in this session.
“So Welcome, friends, enemies, and adtech executives. Today we’re talking about something radical: what if you used your computer… without being watched like a zoo animal?”

“Terms and conditions may apply — to your soul.”
“If you’ve ever actually read a privacy policy, first — seek help. Second — you probably noticed it’s less a contract and more a permission slip for data abuse.”
“We’ve optimized the digital world to be so easy, it’s also easy to exploit. It’s like fast food — tasty now, cardiovascular disaster later.”
Examples:
- Google Docs suggests a title for your therapy notes.
- Auto-fill passwords: helping hackers since 2007.
- Calendar syncs before you hit save.
The Mindset Shift
If your threat model is nation-states,well this post wont be much of use & you really need to be thinking hard (like obtaining separate devices and changing their MAC’s). If your threat model is just “I like to be anonymous” then a decent VPN will do the trick without all the issues with Tor.
“You don’t have to be a hacker — you just need to stop being a willing participant in your own digital surveillance.”
Core ideas:
- Use software that respects you
- Don’t be a default user
- Read the settings once — it’s not that hard
- Don’t be a default user!
- Let me re-iterate: Don’t be a default user, but act like a default user.

“The cloud is just someone else’s computer, except they’re charging rent and going through your drawers.”
Passive Security, Active Tools (Overview)
Switching out your everyday tools for a software that does not phone home and does not have telemetry shipped by default.
Web Browsing
Tool Examples:
- Firefox + uBlock Origin: Blocks ads, trackers, malware
- Librewolf: Privacy focused fork of Firefox
- Brave Browser: Another privacy focused web browser
- Privacy Badger (EFF): Learns to block new trackers
- Cover Your Tracks (EFF): https://coveryourtracks.eff.org
Browser Hygiene
Even with Tor/VPN, your browser itself can give you away via cookies or fingerprinting. Use privacy-focused browsers like Firefox (with privacy extensions) ,Brave, or hardened versions like the Tor Browser for sensitive sessions. Install tracker-blockers like uBlock Origin or Privacy Badger to cut off tracking scripts that attempt to identify you across sites. Also, get in the habit of clearing cookies or using private browsing mode for activities where you log in to an account you don’t want linked to other browsing.

Use search engines like DuckDuckGo,Startpage or even a privacy focused metasearch engine like SearXNG that uses major web search engines but anonymizes queries by fetching your queries through a reverse proxy. And when I say use, I mean set one as your default. Set it and forget it.
For example, don’t do your privacy-sensitive searches in the same
browser session where you’re logged into your personal Google or Facebook account –
that links your secret and public identity. Either use separate browsers or at least
separate profiles/containers (Firefox has Multi-Account Containers extension to isolate
contexts). If you gonna use Facebook do it only from one computer don’t use the Phone App,
use the Facebook container add-on that protects you from the FB pixel installed on many sites that tracks you. This separation is a tool in itself.
Block first, ask questions later. Your browser should be boring to advertisers!!
Productivity Without Paranoia
Tools:
- LibreOffice: No telemetry, open formats
- CryptPad / OnlyOffice: Online collaboration without data mining
“LibreOffice doesn’t ask for your location or try to sync your grocery list to the cloud. Shocking, right?”
VPNs That Don’t Suck
Now VPNs have increased in popularity in recent years but not all VPNs are created equal.
Everything is logged online it’s a matter where you lay your trust in. A good read on this subject is the essay by Ken Thompson (yes that Thompson,co-created Unix) “Reflections on Trusting Trust” that refers to the concept of computer security by highlighting the risks of trusting software tools like compilers. It illustrates how a compromised compiler can insert hidden backdoors into software, making it difficult to ensure the integrity of the code produced. Link to paper
So personally I can only recommend:
- Mullvad: No logs, anonymous sign-up, accepts cash
- Pi-VPN: Run your own VPN service right from your Raspberry Pi.
Use A Password Manager
Try to avoid using online password managers, because of these wise words:
“Regardless of the hardware, service, or encoding Connect it to the internet, and someone’s gonna own it”
Dual Core - All The Things
Tool:
- KeePassXC - Offline
File Sync Without Cloud Nonsense
Tool:
- Syncthing: Sync your files directly between devices. No servers. No snooping.

“If Dropbox and rsync had a baby — and the baby respected your privacy — that’s Syncthing.”
Home Lab
@Your Home/Office
Now in the recent decade micro computers have become widely used.One device that fits this category is the Raspberry Pi. And with harnessing this micro computers power it’s even easier to build a homelab for everything you need.
The concept of homelabbing is the practice of setting up a personal server or multiple servers at home to experiment with various technologies, configurations, applications, and systems.
With this notion in mind you can say run a network wide ad-blocker at the DNS level where every device on your network receives ad-blocking.
After all it’s YOUR network and you can block at your hearts content.
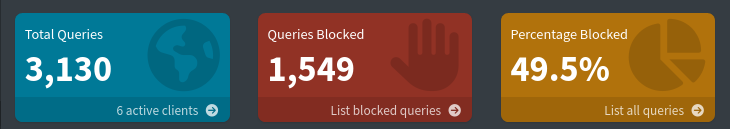
Tool - Pihole: Network-wide Ad Blocking
A Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole and optionally a DHCP server, intended for use on a private network. It is designed for low-power embedded devices with network capability, such as the Raspberry Pi, but can be installed on almost any Linux system. As well as importing externally prepared block-lists, Pi-hole can be configured to block specific websites or apply parental controls. Wikipedia
Consider an alternative OS

Saying an alternative OS makes me cringe personally because I’ve been using an “alternative OS” for over 15 years as a daily driver and more than 20 years in one way or an other. But I can understand that for some if this is the first time breaking away from what a billion company puts in front of them and say:
Here use this, it’s the best Operating System you will ever need.
While that OS is loaded with telemetry tools that records your every keyboard stroke and everything you click. Sending it back to HQ, to be then be dissected behaviorally and sold off .
By switching you are depraving said company of your precious information. That’s the biggest FUCK YOU you can do. A middle finger that can be felt, because overtime it hurts where it matters the most, their pockets.
Yes said companies are Microsoft & Apple, Google too but the choke it has on information via their “web services” makes them equally evil. Ironic for a company having a motto “Don’t be evil”.
On to our subject of “alternative OS”
Switching out Windows or Mac OS with Linux.
This is not how to install Linux but a reminder that be switching Operating System you stop in some manner being an active participant on selling your self out to these companies & selling your self short by self spying. All that data you generate is dollar signs.
Some will say that Linux has been compromised and it might be true but there is no evidence backing this up. Also that it has been bought out via the Linux Foundation and M$ is one of it’s top donations contributor.
The BSD’s of this world
- Open BSD
- Free BSD
Quite smaller projects less popular than Linux, does stuff a bit different but abides with the Unix philosophy. After all Linux is just a free Unix replacement. Since Unix back in the day was proprietary and had insane licensing fee’s.
All of the above may seem mundane and boring to a user that just want’s get work done and get on with life and that’s the CATCH 22 , their betting YOU won’t take another look and continue to be an obedient user.
Prove them wrong and start talking one service at a time back under your control. It’s a long way but it’s worth it. You need to config once then it’s just a file you can restore.
As it is know in the *nix Operating Systems world “everything is a file”.
Digital Detox Plan (Lazy Edition)
| Task | Tool |
|---|---|
| Safer Browsing | Firefox + uBlock + Privacy Badger |
| Safer Browsing 2nd option | Librewolf: All in one privacy browser |
| Safer Browsing 3rd option | Brave Browser |
| Encrypted Messaging | Signal |
| No-Snoop VPN | Mullvad |
| Self-hosted VPN | Pi-VPN |
| Network wide ad-blocker | Pi-Hole (DHCP & DNS servers included) |
| Password Management | KeePassXC |
| Private File Sync | Syncthing |
| No telemetry Work | LibreOffice |
| Online collaboration without data mining | CryptPad / OnlyOffice |
| Bloat-Free OS (Optional) | Fedora / Debian Linux / Some BSD |
If this seems like a full time job, to keep up with privacy and security on your devices. Keep in mind that for some, it’s their full time job to rob you and mine off you anything they can sell to any company willing to put up the $$$ to buy up your browsing habits.
Your data in the new currency and data brokers are making millions off it.
Your New Mantra
“Change your tools.”
“Change your habits.”
“Change your assumptions.”
“You don’t have to go off-grid — just off-default.”
Resources
- https://ssd.eff.org – Surveillance Self-Defense
- https://www.eff.org/privacybadger - Learns to block new trackers
- https://mullvad.net - No logs, no snoop VPN
- https://libreoffice.org - Private Productivity
- https://syncthing.net - Sync your devices privately
- https://debian.org - The Universal OS
- Pi-hole - Local network wide ad-blocker
- PIVPN - Self hosted VPN service
- The Electronic Frontier Foundation
- Firefox Extensions